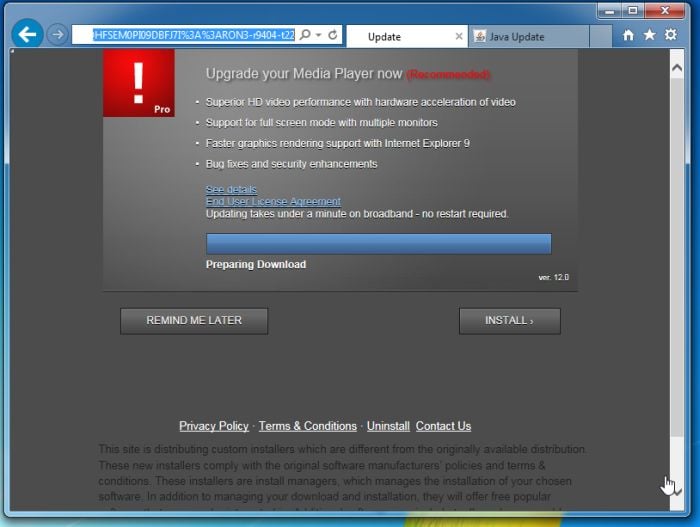
No. 1: Ransom Message
This is the heyday of ransomware, malware that locks up your precious data and asks for a payment using online currency to get it back. If you’re lucky, that ransomware message might go away with a quick reboot – some of the ransomware messages come from programs that don’t lock up your data (known as scareware). If that reboot comes back to the same ransomware screen or you can’t access your data, you have a few options.
What to do: First, if you’ve got a good, recent data backup, all you have to do is recover your computer and restore the data. If you belong to a file storage cloud service, there is a good chance it has backup copies of your data. Don’t be overly confident. Not all cloud storage services have the ability to recover from ransomware attacks, and some services don’t cover all file types. Consider contacting your cloud-based file service directly, via email or phone, and explain your situation. Sometimes tech support can recover your files, and more of them, than you can yourself.
If you don’t have a data backup, decide whether you’re going to pay the ransom. Security experts will tell you never to pay the ransom and scare you with stories of how the ransom was paid and the data was still left locked, but in the vast majority of cases of people who pay the ransom, an encryption code that unlocks the data is sent. I’ve never faced the scenario because I back up my data to multiple places every day, but there’s a good chance I would pay the ransom as a last resort and hope for the best.
Lastly, several sites on the Internet may be able to help you recover your files without paying the ransom. Either they’ve figured out the shared secret encryption key or some other way to reverse engineer the ransomware program. Sometimes ransomware creators even apologize and post recovery keys.
Looking for the best ransomware site can be helped if you can identify the exact ransomware program and version of it you are facing. An updated antimalware program might identify the culprit, although often all you have to go on is the ransomware extortion message, but that is often enough. Then search on that name and version and see what you find.
Normally, you get hit by ransomware because you got tricked into running something you shouldn’t have or you were missing a critical security patch. Resolve not to make the same mistakes again.
No. 2: Fake antivirus messages
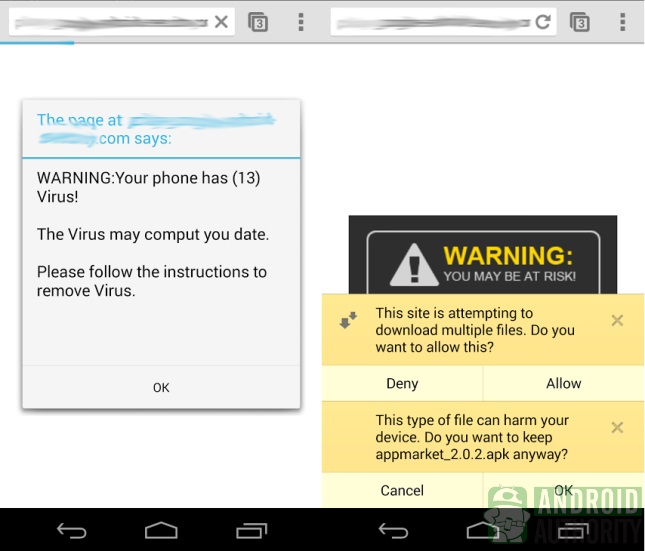
In moderate decline these days, fake antivirus warning messages are among the surest signs that your system has been compromised. What most people don't realize is that by the time they see the fake antivirus warning, the damage has been done. Clicking No or Cancel to stop the fake virus scan is too little, too late. The malicious software has already made use of unpatched software, often a browser add-on program, to completely exploit your system.
Why does the malicious program bother with the "antivirus warning"? This is because the fake scan, which always finds tons of "viruses," is a lure to buy their product. Clicking on the provided link sends you to a professional-looking website, complete with glowing letters of recommendation. There, they ask you for your credit card number and billing information. You'd be surprised how many people get tricked into providing personal financial information. The bad guys gain complete control of your system and get your credit card or banking information. For bad guys, it's the Holy Grail of hacking.
What to do: As soon as you notice the fake antivirus warning message, power down your computer. (Note: This requires knowing what your legitimate antivirus program's warning looks like.) If you need to save anything and can do it, do so. But the sooner you power off your computer, the better. Boot up the computer system in Safe Mode, No Networking, and try to uninstall the newly installed software (oftentimes it can be uninstalled like a regular program). Either way, follow up by trying to restore your system to a state previous to the exploitation. If successful, test the computer in regular mode and make sure that the fake antivirus warnings are gone. Then follow up with a complete antivirus scan. The scanner will often find other sneak remnants left behind.
Note: A related scam is the “technical support scam” where an unexpected browser message pops up warning that your computer has been compromised, and to call the toll-free number on your screen to get technical support help. Often the warning claims to be from Microsoft (even if you’re using an Apple computer). These tech support scammers than ask for you to install a program, which then gives them complete access to your system. They will run a fake antivirus, which not surprisingly, finds lots of viruses. They then sell you a program to fix all your problems. All you need to do is give them a credit card to start the process. Luckily, these types of scam warnings can usually be defeated by closing your browser program and avoiding the web site that hosted it upon you or rebooting your computer. Rarely has this type of malware done anything to your computer that requires fixing.
No. 3: Unwanted browser toolbars
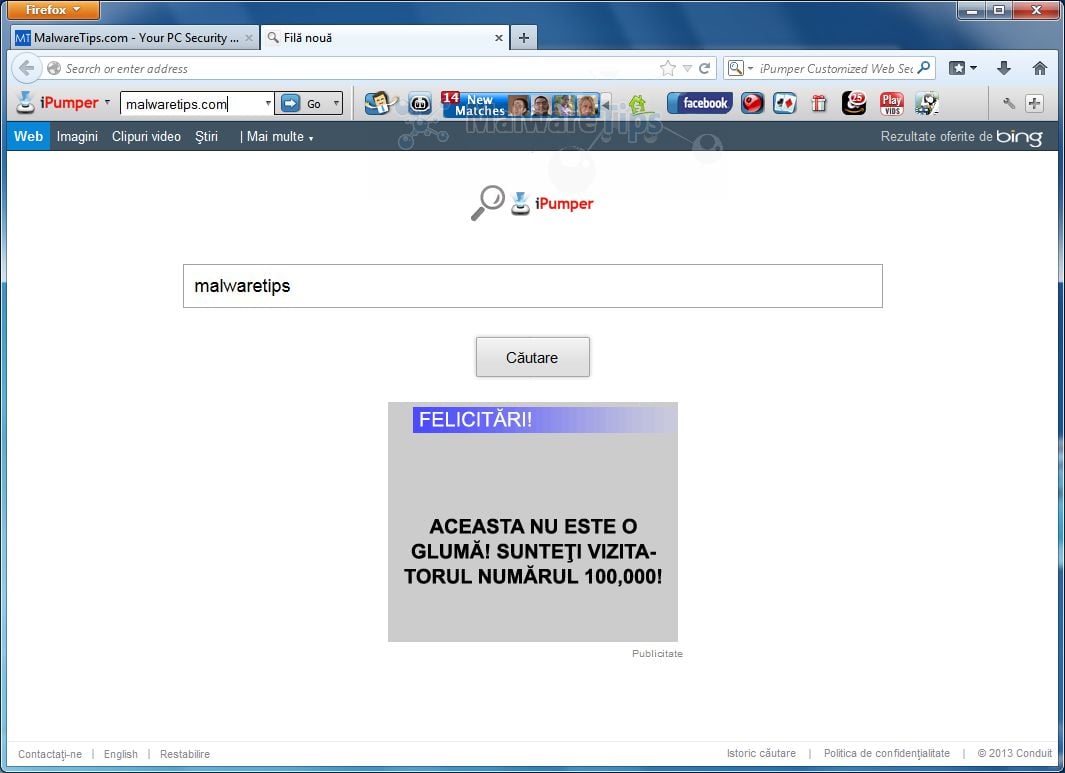
This is a very common sign of exploitation: Your browser has multiple new toolbars with names that seem to indicate the toolbar is supposed to help you. Unless you recognize the toolbar as coming from a very well-known vendor, it's time to dump the bogus toolbar.
What to do: Most browsers allow you to review installed and active toolbars. Remove any you didn't absolutely want to install. When in doubt, remove it. If the bogus toolbar isn't listed there or you can't easily remove it, see if your browser has an option to reset the browser back to its default settings. If this doesn't work, follow the instructions listed above for fake antivirus messages. You can usually avoid malicious toolbars by making sure that all your software is fully patched and by being on the lookout for free software that installs these tool bars. Hint: Read the licensing agreement. Toolbar installs are often pointed out in the licensing agreements that most people don't read.
No. 4: Redirected Internet searches
Many hackers make their living by redirecting your browser somewhere other than you want to go. The hacker gets paid by getting your clicks to appear on someone else's website, often those who don't know that the clicks to their site are from malicious redirection.
You can often spot this type of malware by typing a few related, very common words (for example, "puppy" or "goldfish") into Internet search engines and checking to see whether the same websites appear in the results -- almost always with no actual relevance to your terms. Unfortunately, many of today's redirected Internet searches are well hidden from the user through use of additional proxies, so the bogus results are never returned to alert the user. In general, if you have bogus toolbar programs, you're also being redirected. Technical users who really want to confirm can sniff their own browser or network traffic. The traffic sent and returned will always be distinctly different on a compromised computer vs. an uncompromised computer.
What to do: Follow the same instructions as for removing bogus toolbars and programs. Usually this is enough to get rid of malicious redirection. Also, check your C:\Windows\System32\drivers\etc\hosts file to see if there are any malicious-looking redirections configured within. The hosts file tells your PC where to go when a particular URL is typed in. It’s hardly used anymore. If the filestamp on the host files is anything recent, then it might be maliciously modified. In most cases you can simply rename or delete it without causing a problem.
No. 5: Frequent random popups

This popular sign that you've been hacked is also one of the more annoying ones. When you're getting random browser pop-ups from websites that don't normally generate them, your system has been compromised. I'm constantly amazed about which websites, legitimate and otherwise, can bypass your browser's anti-pop-up mechanisms. It's like battling email spam, but worse.
What to do: Not to sound like a broken record, but typically random pop-ups are generated by one of the three previous malicious mechanisms noted above. You'll need to get rid of bogus toolbars and other programs if you even hope to get rid of the pop-ups.
No. 6: Your friends receive social media invitations from you that you didn’t send

I think we’ve all seen this one before. Either you or your friends receive invitations to “be a friend” when you are already connected friends on that social media site. Usually, you’re thinking, “Why are they inviting me again? Did they unfriend me and I didn’t notice, and now they are re-inviting me” or something similar. Then you notice the new friend’s social media site is devoid of other recognizable friends (or maybe just a few) and none of the older posts. Or your friend is contacting you to find out why you are sending out new friend requests. In either case, the hacker either controls your social media site, has created a second near-look-alike bogus page, or you or friend has installed a rogue social media application.
What to do: The first thing I do is warn other common friends not to accept the unexpected friend request. Say something like, “Don’t accept that new invitation from Bridget. I think she’s hacked!”. And then contact Bridget some other way to confirm. And spread the news in your common social media circles. Next, if not first, contact the social media site and report the site or request as bogus. Each site has their own method for reporting bogus requests, which you can find by searching through their online help. Many times it’s as easy as clicking on a single reporting button. If your social media site is truly hacked (and it isn’t a second bogus look-alike page), you’ll need to change your password (refer to the help information on how to do this if you don’t).
Better yet, don’t waste time. Change your authentication method to be two-factor. That way the bad guys (and rogue apps) can as easily steal and take over your social media presence. Lastly, be very leery of installing any social media application. They are often malicious. Regardless, periodically inspect the installed applications associated with your social media account/page, and remove all but the ones you truly want to have there.
No. 7: Your online password isn’t working
If you are typing in your online password correctly, for sure, and it isn’t working, then you might be hacked. I usually try again in 10-30 minutes, because I’ve had sites experiencing technical difficulties not to accept my valid password for a short period of time. But if you know for sure that your current password is no longer working, then a rogue hacker probably has logged in using it and changed it to keep you out.
In this particular scenario, usually what has happened is that the victim responded to an authentic-looking phish email that purportedly claimed to be from the service that ends up with the changed password. The bad guy collects the logon information, logs on, changes the password (and other information to complicate recovery), and uses the service to steal money from the victim or the victim's acquaintances (while pretending to be the victim).
What to do: If the scam is widespread and many acquaintances you know are being reached out to, immediately notify all your close contacts about your compromised account. Do this to minimize the damage being done to others by your mistake. Second, contact the online service to report the compromised account.
If the compromised logon information is used on other websites, immediately
change those passwords. And be more careful next time. Websites rarely send emails asking you to provide your logon information. When in doubt, go to the website directly (don't use the links sent to you in email) and see if the same information is being requested when you log on using the legitimate method. You can also call the service via their phone line or email them to report the received phish email or to confirm its validity. Lastly, like in the previous compromise scenario, consider using online services that provide two-factor authentication. It makes your account
much harder to steal.
No. 8: Unexpected software installs
Unwanted and unexpected software installs are a big sign that your computer system has likely been hacked. In the early days of malware, most programs were computer viruses, which work by modifying other legitimate programs. They did this to better hide themselves. For whatever reason, most malware programs these days are Trojans and worms, and they typically install themselves like legitimate programs. This may be because their creators are trying to walk a very thin line when the courts catch up to them. They can attempt to say something like, "But we are a legitimate software company." The unwanted software is often legally installed by other programs, so read your license agreements. Frequently, I'll read license agreements that plainly state that they will be installing one or more other programs. Sometimes you can opt out of these other installed programs; other times you can't.
What to do: There are many free programs that show you all your installed programs and let you selectively disable them. My favorite checkers for Microsoft Windows are Microsoft’s free programs,
Autoruns or
Process Explorer. They don't show you every program installed but they will tell you the ones that automatically start themselves when your PC is restarted (Autoruns) or the ones currently running (Process Explorer). Most malware programs will be found embedded in the much larger list of legitimate running programs. The hard part can be determining what is and what isn't legitimate. You can enable the “Check VirusTotal.com” options, and the programs, along with Google’s Virustotal.com web site, will tell you which ones it thinks are malware. When in doubt, disable the unrecognized program, reboot the PC, and re-enable the program only if some needed functionality is no longer working.
No. 9: Your mouse moves between programs and makes correct selections
If your mouse pointer moves itself while making selections that work (this is the important part), you've definitely been hacked. Mouse pointers often move randomly, usually due to hardware problems. If the movements involve making the correct choices to run particular programs, malicious humans are somewhere involved.
Not as common as some of the other attacks, many hackers will break into a computer, wait for it to be idle for a long time (like after midnight), then try to steal your money. Hackers will break into bank accounts and transfer money, trade your stocks, and do all sorts of rogue actions, all designed to lighten your cash load.
What to do: If your computer "comes alive" one night, take a minute before turning it off to determine what the intruders are interested in. Don't let them rob you, but it will be useful to see what things they are looking at and trying to compromise. If you have a cellphone handy, take a few pictures to document their tasks. When it makes sense, power off the computer. Unhook it from the network (or disable the wireless router) and call in the professionals. This is the one time that you're going to need expert help.
Using another known good computer, immediately change all your other logon names and passwords. Check your bank account transaction histories, stock accounts and so on. Consider paying for a credit-monitoring service. If you've been a victim of this attack,
you have to take it seriously. Complete restore of the computer is the only option you should choose for recovery. But if you've lost any money, make sure to let the forensics team make a copy first. If you've suffered a loss, call law enforcement and file a case. You'll need this information to best recover your real money losses, if any.
No. 10: Your antimalware software, Task Manager or Registry Editor is disabled and can't be restarted
This is a huge sign of malicious compromise. If you notice that your antimalware software is disabled and you didn't do it, you're probably exploited -- especially if you try to start Task Manager or Registry Editor and they won't start, start and disappear, or start in a reduced state. This is very common for malware to do.
What to do: You should really perform a complete restore because there is no telling what has happened. If you want to try something less drastic first, try running Autoruns or Process Explorer (or similar programs) root out the malicious program causing the problems. They will usually identify your problem program, which you can then uninstall or delete. If the malware “fights back” and won’t let you easily uninstall them, research the many methods on how to restore the lost functionality (any Internet search engine will return lots of results), then restart your computer in Safe Mode and start the hard work. I say "hard work" because usually it isn't easy or quick. Often, I have to try a handful of different methods to find one that works. Precede restoring your software by getting rid of the malware program, using the methods listed above.
No. 11: Your online account is missing money
I mean lots of money. Online bad guys don't usually steal a little money. They like to transfer everything or nearly everything, often to a foreign exchange or bank. Usually it begins by your computer being compromised or from you responding to a fake phish from your bank or favorite stock trading company. In any case, the bad guys log on to your account, change your contact information, and transfer large sums of money to themselves.
What to do: In most cases you are in luck because most financial institutions will replace the stolen funds (especially if they can stop the transaction before the damage is truly done). However, there have been many cases where the courts have ruled it was the customer's responsibility to not be hacked, and it's up to the financial institution to decide whether they will make restitution to you.
If you're trying to prevent this from happening in the first place, turn on transaction alerts that send text alerts to you when something unusual is happening. Many financial institutions allow you to set thresholds on transaction amounts, and if the threshold is exceeded or it goes to a foreign country, you'll be warned. Unfortunately, many times the bad guys reset the alerts or your contact information before they steal your money. So make sure your financial or trading institution sends you alerts anytime your contact information or alerting choices are changed.
No. 12: You get calls from stores about nonpayment of shipped goods
In this case, hackers have compromised one of your accounts, made a purchase, and had it shipped to someplace other than your house. Oftentimes, the bad guys will order tons of merchandise at the same time, making each business entity think you have enough funds at the beginning, but as each transaction finally pushes through you end up with insufficient funds.
What to do: This is a bad one. First try to think of how your account was compromised. If it was one of the methods above, follow those recommendations. Either way, change all your logon names and passwords (not just the one related to the single compromised account), call law enforcement, get a case going, and start monitoring your credit. You'll probably spend months trying to clear up all the bogus transactions committed in your name, but you should be able to undo most, if not all, of the damage.
Years ago you could be left with a negative credit history that would impact your life for a decade. These days, companies and the credit reporting agencies are more used to cyber crime, and they deal with it better. Still, be aggressive and make sure you follow every bit of advice given to you by law enforcement, the creditors, and the credit-rating agencies (there are three major ones).
Malware vector trifecta to avoid
The hope of an anti-malware program that can perfectly detect malware and malicious hacking is pure folly. Keep an eye out for the common signs and symptoms of your computer being hacked as outlined above. If you are risk-adverse, as I am, always perform a complete computer restore with the event of a breach. Because once your computer has been compromised, the bad guys can do anything and hide anywhere. It's best to just start from scratch.
Most malicious hacking originates from one of three vectors: unpatched software, running Trojan horse programs, and responding to fake phishing emails. Do better at preventing these three things, and you'll be less likely to have to rely on your antimalware software's accuracy -- and luck.